DKIM Explained - How Does It Actually Work?
lemwarm
March 6, 2024
|3 min read
DKIM is an email security protocol that not only provides a layer of security to your emails…
But it also boosts your open rates! 🚀
Why?
Having a well-configured DKIM record set up builds trust with email providers.
As a result, more of your emails will land in your prospects’ inbox.
Many sales teams and other email marketers have their DKIM records in place. Yet, most of them do not know how DKIM works.
We’ll explain all below: ⬇️
What Is DKIM?
DKIM stands for DomainKeys Identified Mail. It’s an email authentication method that uses public and private cryptographic keys to sign emails digitally.
The public key is part of the DKIM record to be added to your domain’s DNS records.
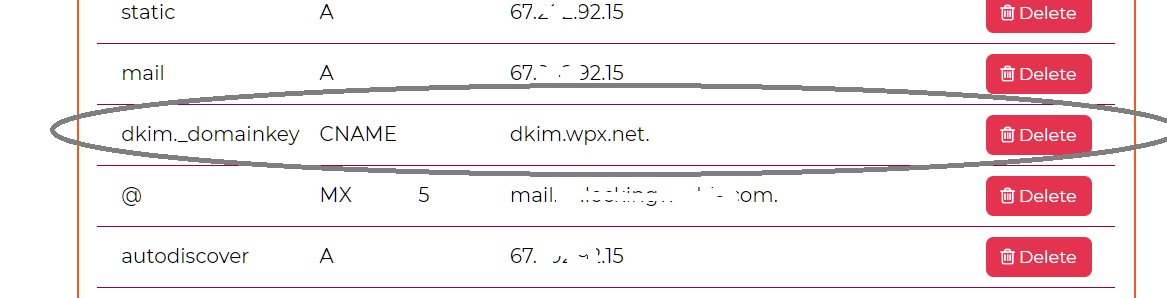
The email sender you use (ESP) is the only party that knows the private key, and uses it to add a signature to the emails you send.
Through the DKIM authentication process, it can be confirmed that an email indeed originated from the claimed domain.
Importantly, it also ensures that the email’s content gets delivered without having been tampered with during transmission.
How Does DKIM Work?
There are three primary parties when considering DKIM:
- You, as the sending domain owner or administrator
- Your email service provider. The ones sending out and digitally signing the emails. In most cases, they will also generate the DKIM record.
- Your domain provider. This is where you add the DKIM record generated by your ESP.
Setting up a DKIM record is as simple as generating a DKIM record (includes public key) through your ESP’s account, adding it to your DNS records, and then returning to your ESP’s account to enable it.
When digitally signing emails, the ESP first decides what data they want to include in their DKIM signatures.
These could be the “from” address, the subject, the body of the email, or others.
If these fields change during transit, the email authentication will fail.
The ESP then creates a hash value for the text fields in the DKIM signature.
The hash string then gets encrypted by the EPS’s private key.
Upon receiving an email, the receiving server can authenticate the signature through the public key by decrypting it back into the original hash.
If the two hashes match exactly, it confirms that the email has not been tampered with during transit.
The email has now been authenticated.
If an email fails authentication, it’s up to the DMARC protocol what to do with the email. The email can either get:
- ➡️ A pass - i.e., it gets delivered normally
- ➡️ Sent to the spam folder
- ➡️ Rejected - the email doesn’t get delivered at all
Why is DKIM Important?
While DKIM’s security isn’t fool-proof it’s still an essential component of your technical email setup.
Here’s why:
- ⚠️It makes it harder for bad guys to abuse your sending domain to send fraudulent emails.
- ⚠️ Implementing DKIM will show you are a legitimate sender, which will improve your sender reputation.
- ⚠️ ESPs will trust your emails more, which boosts your email deliverability, open rates, and overall ROI for your email outreach.
- ⚠️ (Inter)national regulations. DKIM helps you adhere to industry-specific compliance and regulation requirements like GDPR.
Beyond DKIM - Next Steps🚶
DKIM is an important part of your technical setup, yet it is crucial to learn about the other components as well. You’ll also need to know: